Powertech Exit Point Manager for IBM i
Audit and access control through all network services (exit points), including FTP, SFTP, ODBC, etc.
Prevent IBM i Security Breaches:
Protect your organization from the high cost of security breaches by tracking and monitoring data access with Powertech Exit Point Manager for IBM i software. An easy-to-use interface enables administrators to better follow security policy, resulting in a network that’s more secure, more likely to be compliant with regulatory requirements, and less vulnerable to threats.
Control Exit Points:
Secure network access points that traditional menu security plans don’t protect. Safeguard your IBM i systems by closing any and all back doors to the network, including FTP, ODBC, SQL, JDBC, and Remote Command. Monitoring and controlling exit point traffic helps restrict data access only to authorized users.
Limit Access to Sensitive IBM i Data:
Limit access to specific objects and libraries to only the users and groups who have a demonstrated business need. Assign rules by IP address, allowing system access to be limited to approved locations. Easily change and apply rules across your network, with Powertech Exit Point Manager for IBM i.
Maintain an Audit Trail:
Monitor and track users who access data and issue remote commands. Satisfy regulatory initiatives by recording transactions to a secure journal.
What do I get with Powertech Exit Point Manager for IBM i?
Exit Point Control
Control network traffic passing through exit points like FTP, ODBC, JDBC, SQL, and others.
Responsive Browser Interface
Monitor KPIs from your desktop or mobile device without running reports.
Unparalleled Expertise
Partner with industry-leading IBM i security experts.
First-Rate Support
Get your questions answered by a real person 24/7.
Real-Time Notifications
Receive early warnings about network transactions that indicate data is at risk, allowing you to address security concerns before data is compromised.
Key Features:
Track, monitor, and control access to system data. Record user activity, such as who is accessing data and issuing remote commands, in a secure journal. Print reports or analyze data with Microsoft Excel or other tools to more efficiently assess your network security.
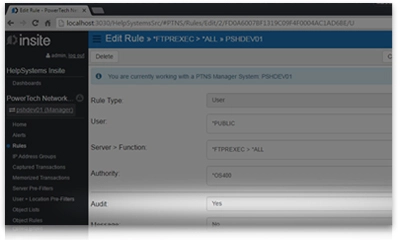
Dynamic rule configuration helps you comply with your security policy. Powertech Exit Point Manager for IBM i allows you to grant access only to users or groups who need it, restrict access to specific objects and libraries, and allow access for only locations approved by policy. Powertech Exit Point Manager for IBM i allows multiple levels of access control, giving you the flexibility to meet your specific requirements.
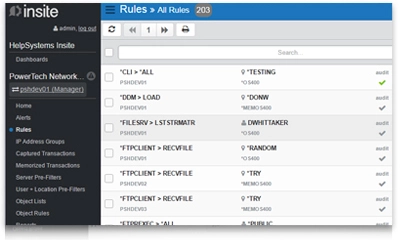
Control access to your IBM i by monitoring and restricting exit point traffic. With Powertech Exit Point Manager for IBM i, you can limit data access to only users who are authorized to download or upload it.
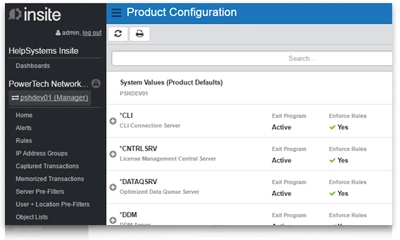
Network transactions may indicate that critical data is at risk. When these events occur, Network Security will send messages to network administrators in real time, helping you address security concerns before data is compromised.
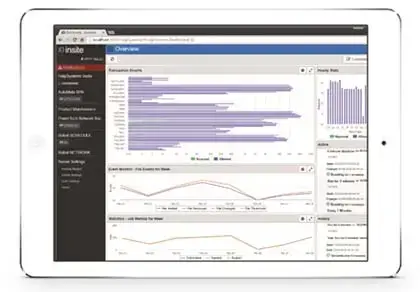
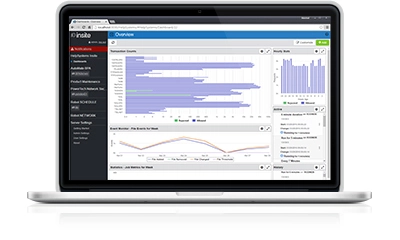
Get greater visibility to key performance indicators with Insite. Dashboards display transaction values without running reports, so you never risk missing issues because you didn’t have time to create a report. Enhanced filtering and search functionality helps you find the information you need quickly. Plus, the mobile-friendly interface provides easy navigation on any device.
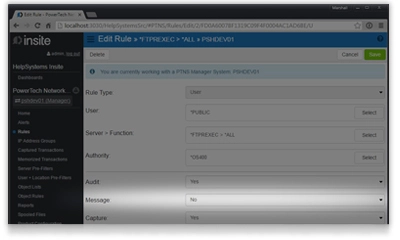
Configure rules and settings just once on the management system. Copy them to other endpoints, quickly propagating your security policy across your network. User-friendly dashboards show you at a glance what’s happening across your network.
Reference Material
Information (Web Site)
Note 1: Some of the content (images and texts) used in this page are property of Fortra